A 'rootkit detection tool', if you were to find such a thing, could only identify something known to alter macOS 'Sierra'. Since there is nothing known that can do that, it's a waste of time to even look for one. Please read About System Integrity Protection on your Mac - Apple Support. Rootkits or rootkit enabling functionality may reside at the user or kernel level in the operating system or lower, to include a hypervisor, Master Boot Record, or System Firmware. Rootkits have been seen for Windows, Linux, and Mac OS X systems.
Try Norton 360 FREE 30-Day Trial* - Includes Norton Secure VPN
30 days of FREE* comprehensive antivirus, device security and online privacy with Norton Secure VPN.
*Terms Apply
Computer viruses and other malware are real threats. And rootkits might be the most dangerous, both in the damage they can cause and the difficulty you might have in finding and removing them.
Rootkits are a type of malware that are designed so that they can remain hidden on your computer. But while you might not notice them, they are active. Rootkits give cybercriminals the ability to remotely control your computer.
Rootkits can contain a number of tools, ranging from programs that allow hackers to steal your passwords to modules that make it easy for them to steal your credit card or online banking information. Rootkits can also give hackers the ability to subvert or disable security software and track the keys you tap on your keyword, making it easy for criminals to steal your personal information.
Because rootkits can hijack or subvert security software, they are especially hard to detect, making it likely that this type of malware could live on your computer for a long time causing significant damage. Sometimes the only way to completely eliminate a well-hidden rootkit is to erase your computer’s operating system and rebuild from scratch.
How do rootkits get on your computer? You might open an email and download a file that looks safe but is actually a virus. You might also accidentally download a rootkit through an infected mobile app.
Here is a look at the different types of rootkits and how you can help protect against them.
Types of rootkits
Mac Rootkit Remover
Here are five types of rootkits.
1. Hardware or firmware rootkit
The name of this type of rootkit comes from where it is installed on your computer. This type of malware could infect your computer’s hard drive or its system BIOS, the software that is installed on a small memory chip in your computer’s motherboard. It can even infect your router. Hackers can use these rootkits to intercept data written on the disk.
2. Bootloader rootkit
Your computer’s bootloader is an important tool. It loads your computer’s operating system when you turn the machine on. A bootloader toolkit, then, attacks this system, replacing your computer’s legitimate bootloader with a hacked one. This means that this rootkit is activated even before your computer’s operating system turns on.
3. Memory rootkit
This type of rootkit hides in your computer’s RAM, or Random Access Memory. These rootkits will carry out harmful activities in the background. The good news? These rootkits have a short lifespan. They only live in your computer’s RAM and will disappear once you reboot your system — though sometimes further work is required to get rid of them.
4. Application rootkit
Application rootkits replace standard files in your computer with rootkit files. They might also change the way standard applications work. These rootkits might infect programs such as Word, Paint, or Notepad. Every time you run these programs, you will give hackers access to your computer. The challenge here is that the infected programs will still run normally, making it difficult for users to detect the rootkit.
5. Kernel mode rootkits
These rootkits target the core of your computer’s operating system. Cybercriminals can use these to change how your operating system functions. They just need to add their own code to it. This can give them easy access to your computer and make it easy for them to steal your personal information.
How to defend against rootkits
Because rootkits are so dangerous, and so difficult to detect, it’s important to exercise caution when surfing the internet or downloading programs. There is no way to magically protect yourself from all rootkits.
Fortunately, you can increase your odds of avoiding these attacks by following the same common-sense strategies you take to avoid all computer viruses, including these.
Don't ignore updates
Updates to your computer’s applications and operating system can be annoying, especially when it seems as if there’s a new update for you to approve every time you turn on your machine. But don't ignore these updates. Keeping your operating systems, antivirus software, and other applications updated is the best way to protect yourself from rootkits.
Watch out for phishing emails
Phishing emails are sent by scammers who want to trick you into providing them your financial information or downloading malicious software, such as rootkits, onto your computer. Often, these emails will look like they come from a legitimate bank or credit card provider. These messages may state that your account is about to be frozen or that you need to verify your identity. The messages will also ask that you click on a link.
If you do, you’ll be taken to a fake website. Once there, you might accidentally download a rootkit to your computer.
The lesson? Never click on any links supposedly sent from a financial services company. If the message is supposedly coming from a company with which you have no accounts, delete them. If the message comes from a company you do business with, log into your online account or call the company. If there’s really a problem, it should show up on your online account or a customer-service representative will confirm it.
Be careful of drive-by downloads
Iphone Rootkit
Drive-by downloads can be especially troublesome. These happen when you visit a website and it automatically installs malware on your computer. You don’t have to click on anything or download anything from the site for this to happen. And it’s not just suspicious websites that can cause this. Hackers can embed malicious code in legitimate sites to cause these automatic downloads.
The best way to help protect yourself? Approve updates to your computer’s software quickly. Set your operating system, browsers, and all applications to install updates automatically so that your computer systems will always have the most up-to-date protections in place.
Don’t download files sent by people you don’t know
Be careful, too, when opening attachments. Don’t open attachments sent to you by people you don’t know. Doing so could cause a rootkit to be installed in your computer.
If you receive a suspicious attachment? Delete the email message immediately.
Try Norton 360 FREE 30-Day Trial* - Includes Norton Secure VPN
30 days of FREE* comprehensive antivirus, device security and online privacy with Norton Secure VPN.
*Terms Apply
The Rootkit Mac Os Catalina
Editorial note: Our articles provide educational information for you. NortonLifeLock offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about cyber safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses.
Copyright © 2021 NortonLifeLock Inc. All rights reserved. NortonLifeLock, the NortonLifeLock Logo, the Checkmark Logo, Norton, LifeLock, and the LockMan Logo are trademarks or registered trademarks of NortonLifeLock Inc. or its affiliates in the United States and other countries. Firefox is a trademark of Mozilla Foundation. Android, Google Chrome, Google Play and the Google Play logo are trademarks of Google, LLC. Mac, iPhone, iPad, Apple and the Apple logo are trademarks of Apple Inc., registered in the U.S. and other countries. App Store is a service mark of Apple Inc. Alexa and all related logos are trademarks of Amazon.com, Inc. or its affiliates. Microsoft and the Window logo are trademarks of Microsoft Corporation in the U.S. and other countries. The Android robot is reproduced or modified from work created and shared by Google and used according to terms described in the Creative Commons 3.0 Attribution License. Other names may be trademarks of their respective owners.
What is the ESET Mac Rootkit Detector?
ESET Mac Rootkit Detector is a small app file. After download, it will scan your Mac running macOS for rootkits. It provides a single-click way to check your macOS for rootkits.
What can a rootkit do?
A rootkit is a stealthy type of malicious software designed to lie hidden on computers and remain undetected by antivirus software. It enables continued administrative access to a computer, allowing access to your personal information. Rootkits are frequently used in combination with other malware to hide them from users and security products.
Why do I need this?
The code for creating rootkit is nowadays available online. This increases the likelihood of finding rootkits for macOS in the wild.
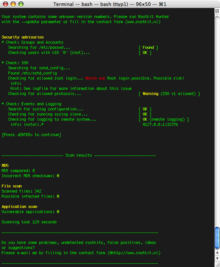
ESET Mac Rootkit Detector provides a user friendly way to check the integrity of the kernel memory and give information to the user about potential problems.
Why did we develop ESET Mac Rootkit Detector?
In the last year we have seen rootkit targeting macOS and keeping users safe while online is our mission. Therefore we decided to develop ESET Mac Rootkit Detector and protect our users from rootkits like macOS/Crisis (macOS/Morcut) that was used to spy users and steal information from the macOS.
Operating Systems:
- macOS X 10.8.x (Mountain Lion)
- macOS X 10.7.x (Lion)
- macOS X 10.6.x (Snow Leopard)
Processor Architecture:
32bit x86 or 64bit x64, Intel®